Setting up SSL for a Node server running on Synology Diskstation
This page provides information on how I configured a new SSL for a node server I have running on my Synology DiskStation (aka NAS). This is Part 2 in the series and assumes certain configurations described there. Refer to Part 1.
Goal
I want to have the website I'm hosting on my home NAS to be accessible securely via HTTPS, as a subdomain to my NAS domain.
The problem? My domain has a standard SSL certificate, which only covers the top-level domain and the www subdomain. Any subdomains either need to get their own certificates, or the top-level domain needs a wildcard certificate, which is quite expensive.
The solution? Use free certificates from Let's Encrypt. They are legit. The only downside is that the certificates have to bew renewed every 3 months, but this can be automated.
Below, I will describe the steps to get an SSL for the subdomain (while keeping my existing SSL certificate for the root domain) and how to configure everything to make it work.
A note on my existing configuration
Hardware
I have a Synology DS416Play for my NAS (Network Access Storage). It's connected to a Ubiquiti UniFi Dream Machine Pro as the router.
Network
My domain is registered by GoDaddy. I have a Standard SSL certificate for this domain issued by GoDaddy. I can manage these SSLs here.
The DNS settings can be found under DNS Management. The A record, which has a name of @, is set to the WAN IP number of my router. For subdomains, the CNAME is used. I already have www configured to point to @.
The WAN IP can be retrieved using the Network application at unifi.ui.com from the Internet section.
The DHCP on the router is configured to give the NAS always the same LAN IP (192.168.1.32). This is done in the Network application, under Client Devices. Search for the Synology device, select it and use Settings to enable Fixed IP.
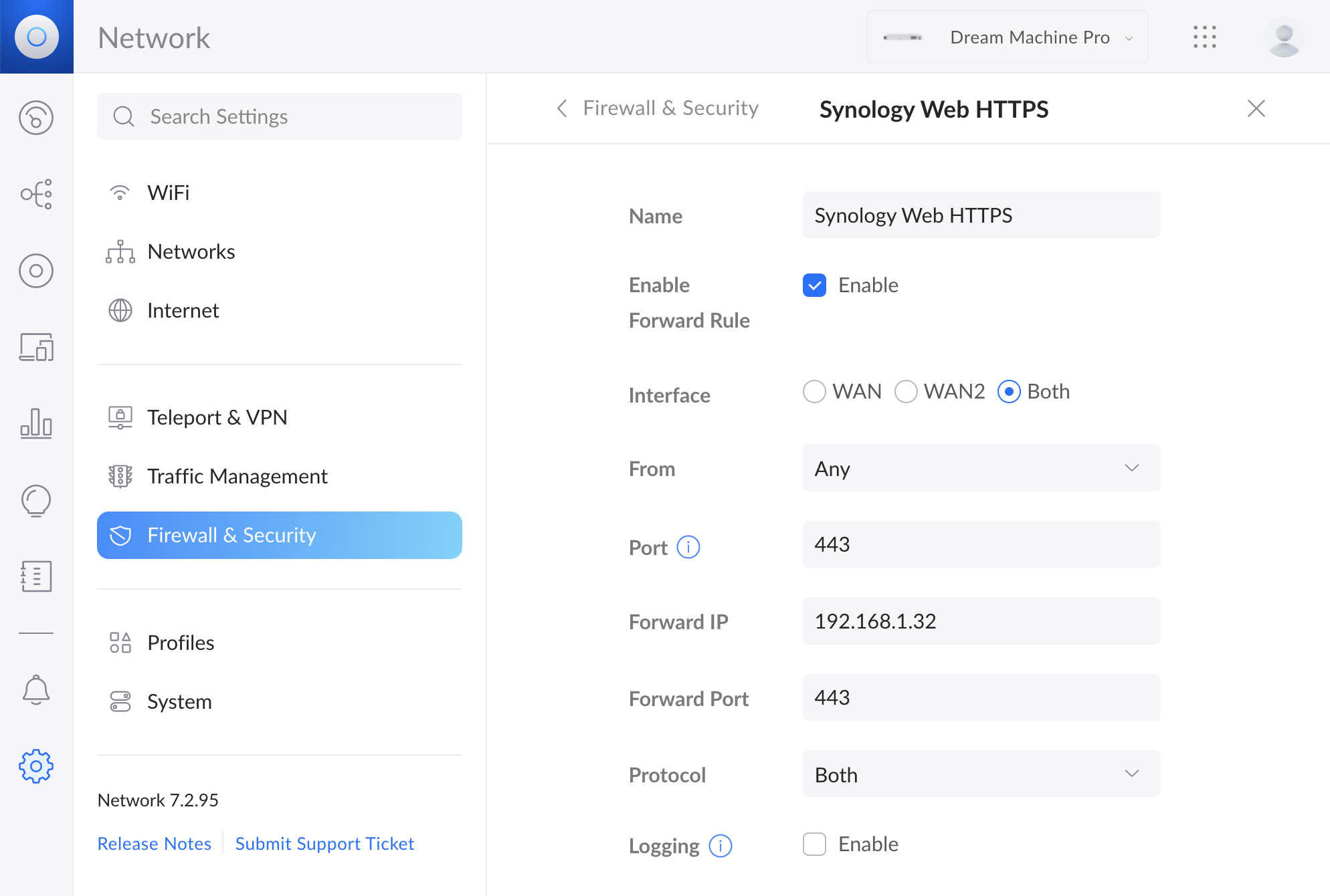
The router is also configured to route HTTP and HTTPS requests (at port 80 and 443, respectively) to the same PORT on the LAN IP address of the NAS. This is done in the Network appplication, under Firewall & Security in Port Forwarding.
Software
On the NAS, I'm running DSM 6.2.4-25556 Update 6. I have the following packages installed:
- Web Station 2.1.10-0160
- Node.js v12
- Node.js v8 (probably not needed)
Steps
1. On the NAS
- Go to the Web Station, under General Settings, set HTTP back-end server to Nginx.
- Go to the Control Panel > Application Portal
- Select the Reverse Proxy tab.
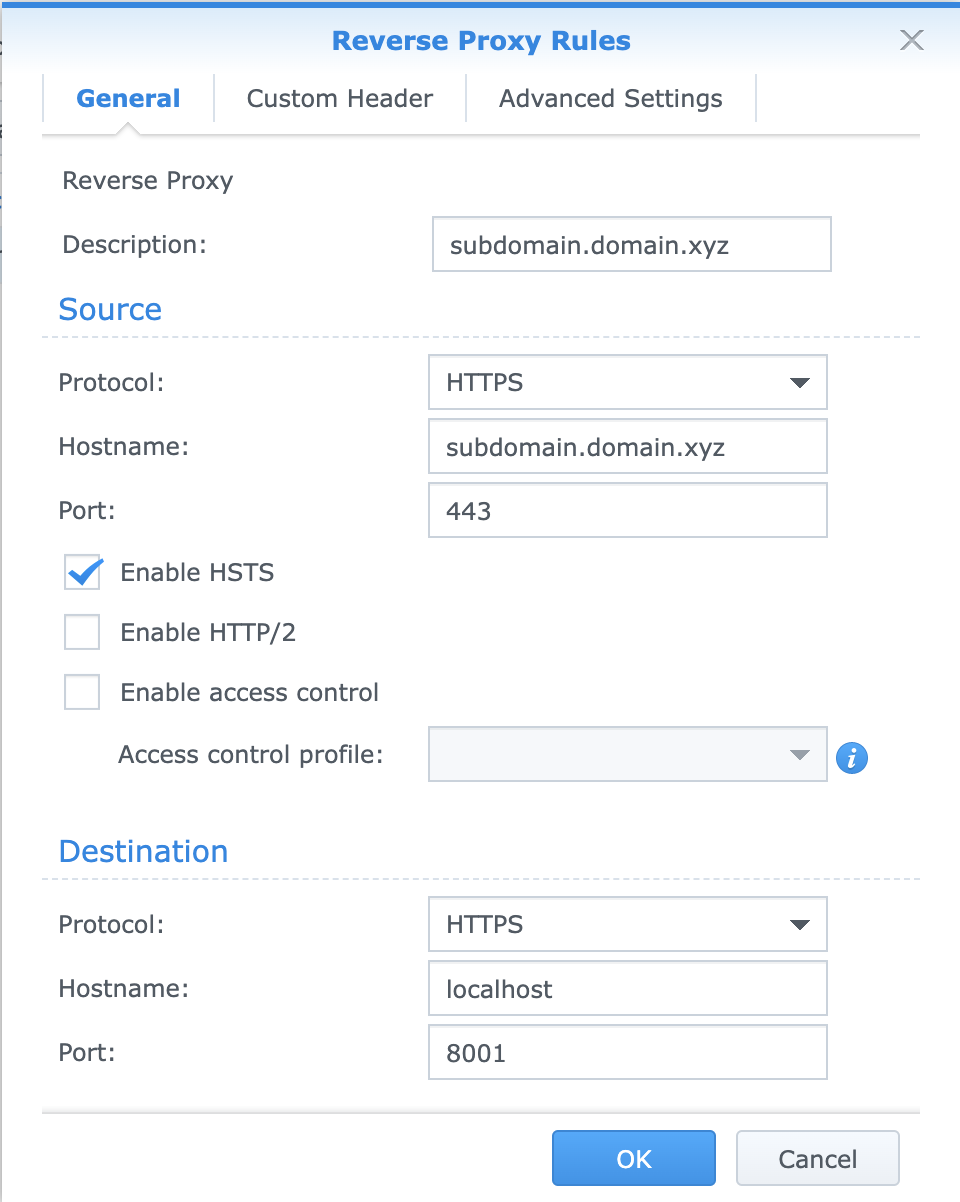
- Create a new entry for the new web service.
- Set the Source protocol to
HTTPS, the hostname to the full domain name, and the port to443. I also checkedEnable HSTS, so that any HTTP requests are automatically renegotiated to HTTPS. - Set the Destination protocol to
HTTPS, the hotname tolocalhost, and the port to the local PORT you're running the service. (e.g. 8001)
- Set the Source protocol to
- Select the Reverse Proxy tab.
- Go to the Control Panel > Security
- Select the Certificate tab.
- Add a new certificate
- Select
Get a certificate from Let's Encrypt.- As the Domain name, put in the root domain name. (e.g.
domain.ext) - Enter your email
- As the Subject Alternative Name, put in the full domain name (e.g.
subdomain.domain.ext) - Wait about a minute or two for the cert to be generated.
- As the Domain name, put in the root domain name. (e.g.
- To download the certificate:
- Select the newly added certificate (issued by R3).
- Click the little dropdown icon in the Add button
- Select Export certificate.
- Open the downloaded file
archive.zipto extract the files. If you're on macOS, this will extract the files to~/Downloads/archive. We will use these files in our Node service in the next section.
- Click Configure
- For the entry that corresponds to your node service, ensure in the certificate dropdown that the new certificate is selected.
2. On your local dev machine
- Open a terminal
cd ~/HOSTNAME/SHARE/certcp ~/Downloads/archive/*.* .- assuming this is where the certificate ZIP file was extracted to- Modify your Node project to refer to the correct files, e.g.
const certPath = path.join(__dirname, '..', 'cert'); const httpsOptions = { key: readFile(certPath, 'privkey.pem'), cert: readFile(certPath, 'cert.pem') }; // options to be used with https.createServer() ssh HOSTNAME -p 220- where HOSTNAME is the local name of your NAScd /volume1/SHARE/web- where the path is configured according to nas-node.md- Start your node server. Pay attention to which port it uses.
Summary
If everything has worked well, when you go to https://yoursubdomain.yourdomain.yourext in a browser, the request should work without any certificate issues. This is my understanding of what is basically happening when you make this request:
- The browser checks the DNS for the FQDN.
- The DNS records, as configured by the domain registrar (in my case GoDaddy) maps the FQDN to an IP number.
- The browser makes the request to the IP number at port 443, which is implied by the HTTPS request.
- The home router receives and redirects the request at port 443 to the LAN IP address of the NAS as configured in its Port Forwarding rules.
- On the NAS, Nginx receives the request. Since it's an HTTPS request, it checks the certificates for this FQDN.
- Once certificates are validated, the request is sent to
https://localhost:8001as configured in the reverse proxy configuration. - Our Node service receives the request. The Node HTTPS server checks the request against the local certificates we have configured it with, and serves the traffic normally.